Blogger: Kevin Coulson, APR, Gainesville Chapter
Eric Kron has spent more than 20 years in the information security field. With experience that across multiple fields, he’s developed a deep understanding of the grim realities that businesses face in our ever-connected world.
The facts
As employees, you are the last line of defense:
- 91% of successful data breaches started with a spear phishing attack
- Ransomware was a 1 Billion dollar criminal business in 2016
- CEO Fraud (aka business email compromise) causes $5.3 B in damages
- W-2 Scams social engineer Accounting/HR to send tax forms to the bad guys
The costs of breaches and ransomware attacks:
- There was a 752% increase in the new ransomware families in 2016
- Ransomware caused about $1B in losses in 2016
- Over 153,000 users were hit by mobile ransomware in 2016
- Ransomware price tags shot up by a staggering 266% to $1,077 on average in 2016 [slide]
- A typical attack takes 32 hours of labor to resolve
- Less than half that paid (45%) got their information back
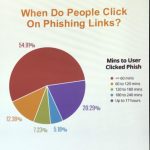
Recent studies show that over 54.9% of users click on a phishing link in less than 60 minutes.
Basic methods of social engineering
- Making the situation uncomfortable
- Social mores, e.g. the obligation to open a door for someone if they just opened a door for you
- Clickbait: it’s more science than you think [slide]
- Leverages “pattern interruption” to create curiosity/exploit information gaps
- Uses emotion
Remote attacks
- Phishing
- Vishing (voice phishing)
- Smishing (SMS/text phishing)
Criminals are doubling up on these to make the scam seem more legitimate, e.g. a phishing email followed by smishing text.
If you click on a link and it asks you to retype your password, take warning.
LinkedIn attacks are on the rise as it is a common method for professionals to connect.
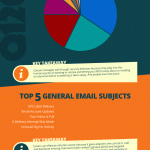
Common Phishing Scams
The invoice/PO Phish, e.g. “your invoice is attached” or “please see the attached purchase order”, is the most common phishing genre reported via KnowBe4’s Phish Alert Button. This type of phish easily blends into the deluge of emails that employees in many positions deal with on a daily basis.
The package or parcel delivery phish presents fake tracking or delivery updated information. This is especially prevalent in companies that ship/receive as part of their business.
The document or file delivery/sharing phish, e.g. emails involving files being shared or delivered through services like Docusign or Dropbox, is common in industries where documents are often shared with some level of encryption.
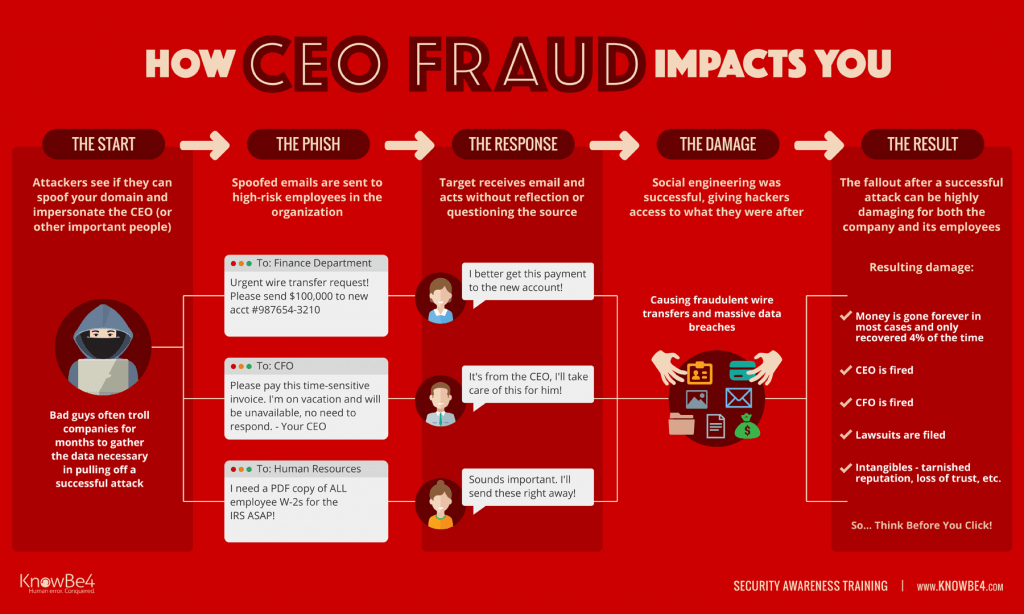
CEO Fraud
Things to watch for:
- If you’re a US-based company, the word “kindly” is a giveaway for CEO fraud emails.
- If something doesn’t seem quite right, check it out in person
- Take note of lookalike URLs, e.g. cnn.com vs. crm.com where the “r” and “m” are meant to look like two “nn”.
Plug-in Attacks
Don’t plug random things into your devices and don’t plug your devices into random things USBs
- USB drives are fast and can hold a lot of data
- University of Illinois Urbana 300 USB dropped around campus 48% plugged them in
- Charging stations
- Use a charge only cord or adapter
Develop a coordinated security awareness campaign
- Most security awareness programs are still too superficial and done for compliance only
- What is missing is the correct estimation of the adversary being faced
- Training once a year isn’t enough
- Simulated phishing emails alone don’t work
- Mix training with simulation with a high-level of repetition.
Finally, when asked about using public Wi-Fi, e.g. at #FPRAAC, Kron suggested using VPNs.
Erich Kron
Security Awareness Advocate